Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
| Excerpt | ||
|---|---|---|
| ||
When OpenVPN is enabled by root360 for specific users, they are able to connect to the bastion host using a TLS-secured private tunnel. |
General process
OpenVPN is disabled by default.
When OpenVPN is enabled by root360 for specific users, they are able to connect to the bastion host using a TLS-secured private tunnel. When additionally Multi-Factor-Authentication (MFA) is active for the environment valid MFA information must be provided upon connect.
Following steps are required to enable and use OpenVPN:
check and accept preconditions
request activation of OpenVPN and optionally MFA
activate MFA if it is enabled
obtain the VPN client config, install and configure OpenVPN client
establish VPN connection
Multi-Factor-Authentication (MFA)
Multi-Factor-Authentication (short MFA) is a method to improve the protection against credential brute-force attacks by requiring multiple security information.
In general the following factor groups exist:
something you know (e.g., password, passphrase, answers to security questions)
something you have (e.g., OTP generator device, SSL certificate)
something you are (e.g., biometric information like fingerprint or iris scan)
When MFA is used at least 2 out of those groups are requested and must be valid to grant access.
For OpenVPN we support MFA by always requiring a valid SSL certificate and additional information. The MFA method is configured globally for every environment.
The following methods are currently support for OpenVPN:
Method 1: Credentials of dashboard (Orbiter) (recommended)
required for PCI DSS environments
Method 2: Time-based one-time-password token (TOTP-token)
We are recommending method 1 because the activation and management processes are easier than method 2. Additionally with this method the user may change the credentials whenever required without depending on our support.
Method 2 is sometimes called 1,5 MFA because on a deeper look TOTP-tokens are in the same factor group as SSL certificates. As TOTP-tokens are valid for a few minutes and the device that generates them is different than the SSL certificate storing device which is why this method still improves the security a lot. It also prevents credential brute-forcing attacks almost equally to method 1.
For compliance regulations like PCI DSS method 2 is not sufficient which is why we are enforcing method 1 for environments with these requirements.
Preconditions (not for site-to-site connection)
When Multi-Factor-Authentication (MFA) should be configured the following preconditions are required.
Method 1: Credentials of dashboard (Orbiter)
Every OpenVPN user must have a verified account for our dashboard (Orbiter).
Method 2: Time-based one-time-password (TOTP) token
See preconditions at Activate MFA (Multi-Factor-Authentication) for SSH and OpenVPN
Request activation of OpenVPN
Request activation of OpenVPN for a dedicated environment via change request at https://support.root360.cloud.
If you want additional security add the requirement for MFA configuration to your activation request.
Activate MFA (not for site-to-site connection)
The activation process depends on the MFA method you choose.
Method 1: Credentials of dashboard (Orbiter)
To use this recommended MFA process you have to request access for every user that should connect to the OpenVPN via https://support.root360.cloud.
Method 2: Time-based one-time-password (TOTP) token
Follow the steps for MFA activation at Activate MFA (Multi-Factor-Authentication) for SSH and OpenVPN , if TOTP-MFA is enabled for the target environment.
Install and configure OpenVPN client
Windows
Download the OpenVPN Windows installer
Install the client software (make sure to tick "EasyRSA
3 Certificate Management Scripts"
 )
)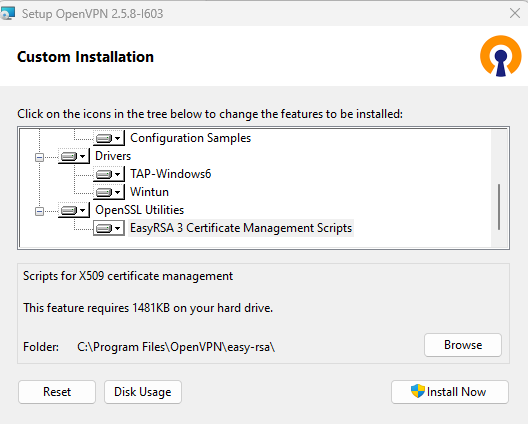 Image Added
Image AddedCreate a Certificate Signing Request (see additional infos below) and send the resulting CSR file to root360 via https://share.root360.cloud/
Get the OpenVPN client config file including the signed certificate from root360
Copy the content of your private key into the config file (into the key section)
Code Block <key> -----BEGIN PRIVATE KEY----- ... -----END PRIVATE KEY----- </key>Copy the secret VPN config file into directory C:\Users\<your-user>\OpenVPN\config
Linux
Install the OpenVPN client and easy-rsa using your package manager
Create a Certificate Signing Request (see additional infos below) and send the resulting CSR file to root360 via https://share.root360.cloud/
Get the OpenVPN client config file including the signed certificate from root360
Copy the content of your private key into the config file (into the key section)
Code Block <key> -----BEGIN PRIVATE KEY----- ... -----END PRIVATE KEY----- </key>Copy the secret VPN config file into a directory of your choice
Establish connection
Windows
Start the programm OpenVPN GUI
Double-click the OpenVPN GUI systray icon (lower right desktop corner) to start the connection
Enter your certificate password and the MFA information
in case of MFA method “credentials of dashboard (Orbiter)”: enter your username and password for Orbiter
in case of MFA method “time bases one-time-password token”: enter the 6 digit based token generated by your TOTP application
Linux - Manual Start
Run OpenVPN client
Code Block openvpn --config /path/to/secret_vpn_configEnter your certificate password and the MFA information
in case of MFA method “credentials of dashboard (Orbiter)”: enter your username and password for Orbiter
in case of MFA method “time bases one-time-password token”: enter the 6 digit based token generated by your TOTP application
Additional information
Create CSR
see example code below for your operating system:
 make sure to replace <username> with your name in format <first-digit-of-prename>_<surname> (e.g. j_doe) AND append the current date in format YYYYMMDD (e.g. 20200103): j_doe_20200103
make sure to replace <username> with your name in format <first-digit-of-prename>_<surname> (e.g. j_doe) AND append the current date in format YYYYMMDD (e.g. 20200103): j_doe_20200103 
we recommend to secure your certificate with a strong password when asked
Enter PEM pass phrase:at least one lower-case character
at least upper-case character
at least one digit
at least 8 characters
optionally with symbols
make sure to set valid values for
Country Name (
<country-code>) = 2-letter code for your companies country, e.g. DEState or Province Name (
<province>) = name of your companies state/province, e.g. SaxonyLocality Name (
<city>) = name of your companies city, e.g. LeipzigOrganization Name (
<company name>) = your company, e.g. root360 GmbHCommon Name (
<username>_YYYYMMDD>) = your VPN username, e.g. j_doe_20200103Email Address (
<email-address>) = your email address registered in root360 cloud dashboard (Orbiter), e.g. j.doe@example.comA challenge password = empty as it does not provide any security improvements for the intended usage
copy the content of
pki\reqs\<your-name>.csr into https://share.root360.cloud/
send the share link into the ticket requesting OpenVPN activation
Sample commands for Windows
| Code Block |
|---|
C:\Users\john.doe> xcopy "C:\Program Files\OpenVPN\easy-rsa" "%USERPROFILE%\Documents\easy-rsa" /I /E C:\Users\john.doe> cd "%USERPROFILE%\Documents\easy-rsa" C:\Users\john.doe\Documents\easy-rsa> init-config.bat "C:\Users\john.doe\Documents\easy-rsa> vars.bat C:\Users\john.doe\Documents\easy-rsa> mkdir keys C:\Users\john.doe\Documents\easy-rsa>Program Files\OpenVPN\easy-rsa\EasyRSA-Start.bat" # ./easyrsa init-pki # sed -i 's/distinguished_name.*=.*/distinguished_name = org/g' pki/safessl-easyrsa.cnf # openssl req -days 3650 -new -keyout keys\<username>pki/private/<username>_YYYYMMDD.key -out keys\<username>pki/reqs/<username>_YYYYMMDD.csr -config openssl-1.0.0pki/safessl-easyrsa.cnf Generating a RSA private key ............+++++ ..........+++++ writing new private key to '<username>.key' Enter PEM pass phrase:********** Verifying - Enter PEM pass phrase:********** ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:<country-code> State or Province Name (full name) [Some-State]:<province> Locality Name (eg, city) []:<city> Organization Name (eg, company) [Internet Widgits Pty Ltd]:<company name> Organizational Unit Name (eg, section) []: Common Name (e.g. server FQDN or YOUR name) []:<username>_YYYYMMDD Email Address []:<email-address> Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: |
Sample commands for Linux
| Code Block |
|---|
$ openssl req -new -keyout <username>.key -out <username>.csr -config /etc/ssl/openssl.cnf Generating a RSA private key ............+++++ ..........+++++ writing new private key to '<username>.key' Enter PEM pass phrase:********** Verifying - Enter PEM pass phrase:********** ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:<country-code> State or Province Name (full name) [Some-State]:<province> Locality Name (eg, city) []:<city> Organization Name (eg, company) [Internet Widgits Pty Ltd]:<company name> Organizational Unit Name (eg, section) []: Common Name (e.g. server FQDN or YOUR name) []:<username>_YYYYMMDD Email Address []:<email-address> Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: |
While running this command the following warning might be printed and can be ignored:
| Code Block |
|---|
Can't load /[...]/.rnd into RNG 140068274860480:error:2406F079:random number generator:RAND_load_file:Cannot open file:../crypto/rand/randfile.c:88:Filename=/[...]/.rnd |
Related tutorials
| Filter by label (Content by label) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
|
Related Components
| Filter by label (Content by label) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
|
| Status | ||||
|---|---|---|---|---|
|
| Table of Contents | ||
|---|---|---|
|
| Filter by label (Content by label) | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
|